PlugX is ready to talk to a command and Command (C2) server once the contaminated Laptop connects to the internet.
The Miniature Aircraft Association of Tri-Metropolitan areas retains a number of fun flies and big chicken occasions each year. Their planes operate within the extremely most straightforward electrical to big chicken to scale using a escalating curiosity in helicopters & 3D planes.
A Variation of “PlugX” malware used by Chinese condition-backed hackers has been deleted from thousands of US personal computers globally next a multi-thirty day period law enforcement Procedure, the US Department of Justice (DoJ) has declared.
As I pointed out in that piece, creating a network of faux carding web sites is the perfect cybercrime. In fact, no person who gets phished or scammed is going to report the criminal offense to your authorities. Nor will any individual assistance the weak sucker who will get snookered by a person of such phony carding web pages. Caveat Emptor!
Safety teams should think about the detective controls they have got in place to identify compromised buyers prior to far too much destruction is completed.
In late 2019, BriansClub modified its homepage to incorporate doctored visuals of my Social Security and copyright playing cards, credit rating report and cellphone bill details. Which was ideal after KrebsOnSecurity broke the news that somebody had hacked BriansClub and siphoned info on 26 million stolen debit and credit accounts.
Moreover, Bclub employs a dispersed community of servers, which makes it resilient to takedown makes an attempt by regulation enforcement agencies.
Dependant upon the entity’s name, the amount of time between this action and when shoppers find out it might be long more than enough to create substantial financial gain.
Now, we’re viewing numerous smaller sized, more qualified market markets coming on the web – which includes automatic botnet marketplaces together with other equivalent enterprises.
“On the other hand, For the reason that desire for stolen charge cards is going up, other distributors will certainly try and capitalize around the disappearance of the best player.”
By 2019 BriansClub experienced develop into amid the biggest carding markets around the dim Net, possessing an inventory of in excess of 26 million stolen credit card documents from various facts breaches.
copyright is definitely improved although the implementation facts I think tend to be more complicated. Is there was a decentralized strategy to for Apple/Android Spend to work globally, I’d support that.
A singular approach to identity danger detection and response (ITDR) may help organizations remediate privileged identity threats and fully grasp the prospective ramifications of compromise, which include entry to significant info and mental home.
Bender reveals the Bodily abuse he and his mom undergo for the brains hands of his father, which include cigar burns, in addition to other accidents he has sustained from his father physically abusing him. He is serving detention for pulling a Phony hearth alarm.
 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Jonathan Lipnicki Then & Now!
Jonathan Lipnicki Then & Now! Earvin Johnson III Then & Now!
Earvin Johnson III Then & Now! Monica Lewinsky Then & Now!
Monica Lewinsky Then & Now!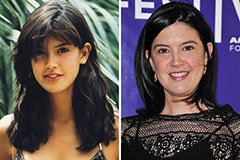 Phoebe Cates Then & Now!
Phoebe Cates Then & Now!