Barysevich explained the lack of a lot of legitimate cards could affect how other carding merchants contend and rate their solutions.
I was preparing to knock off perform with the 7 days on a the latest Friday evening whenever a curious and troublesome e-mail came in via the Call type on This web site:
"We've been examining our present protection policies and possess applied more steps to further more protect from comparable incidents transferring forward," claimed the company.
It's intriguing work even though, specially when you dig into them such as you did. If I ever hit the lotto I will seek the services of another person to go the space and investigate each one, doc, audio report it, etc.
There’s a “basic” solution to this: Give just about every individual in the world a Chip enabled Square (or competitor) product. This solves the world wide web Edition of the condition w/o necessitating inventing new engineering. The expense is huge, but in all probability less costly than upgrading the gasoline stations (I could possibly be Incorrect, we’re speaking say 600 million people today in North The usa, and I’ll naively guess it charges $fifty per reader).
But, being a percentage… copyright (bitcoin precisely) includes a A great deal bigger level of getting used for illegal activity. You will find merely much less legit/legal causes for copyright in currently’s market.
Determining the ruse had long gone also much, I confessed to Mitch that I wasn’t actually the administrator of BriansClub, Which the individual he’d reached out to was an unbiased bclub cm journalist who writes about cybercrime.
Andrei Barysevich, co-founder and CEO at copyright, explained the breach at BriansClub is unquestionably considerable, given that copyright at this time tracks a total of 87 million credit history and debit card data available for sale throughout the cybercrime underground.
marc October seventeen, 2019 Sounds neat, they issue you components that reads your chip and provides a OTP? Do you know of the website page or online video that reveals examples of this?
To continue reaping the rewards of MFA, corporations will have to evaluate their ability to detect account compromise, not just reduce it. Though MFA bypass feels like a comparatively new stability obstacle, the assault chain we are viewing is tried and tested.
Nevertheless, as The brand new vulnerabilities present, MFA does not provide adequate stability By itself. Two key aspects to look at are how the user obtains the secondary authentication process And exactly how easy it's to generally be siphoned with the attacker.
Destructive actors also use ‘sim hijacking,’ wherever they impersonate and obtain Charge of a person’s telephone number. Using your telephone number, hackers can intercept any two-issue authentication codes despatched by text message.
Roger Ebert awarded three stars out of four and called the performances "fantastic", including which the movie was "roughly predictable" but "would not need earthshaking revelations; It is about Youngsters who expand ready to talk to one another, and it has a surprisingly great ear for your way they communicate."[39] Gene Siskel from the Chicago Tribune gave the film three-and-a-50 % stars out of four, and wrote: "This confessional method has worked in films as distinct as Who's Afraid of Virginia Woolf?
The material is slightly talky (albeit not in a method that will result in anyone to confuse it with something by Éric Rohmer), nevertheless it's really hard not to be drawn into the planet of such figures."[forty four]
 Neve Campbell Then & Now!
Neve Campbell Then & Now! Melissa Joan Hart Then & Now!
Melissa Joan Hart Then & Now! Danny Pintauro Then & Now!
Danny Pintauro Then & Now!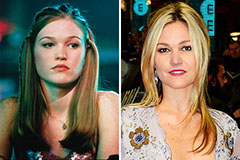 Julia Stiles Then & Now!
Julia Stiles Then & Now! Traci Lords Then & Now!
Traci Lords Then & Now!